Is Mark Zuckerberg really taking classes to make him appear more human? You’ll have to find that out by yourself. In 2018, hackers were able to access Facebook users’ data making it one of the biggest data breaches in history. This would have been prevented if Facebook had used privacy-preserving techniques. For example, Facebook could have used homomorphic encryption to encrypt users’ data before it was stored on their servers. User data can be stored as both encrypted and unencrypted - sensitive data like emails and contact information should always be encrypted.
Other huge data breaches have happened, I’ll list a few:
Fitbit data breach (2023): Hackers stole data from over 10 million Fitbit users, including names, email addresses, dates of birth, and physical activity data.
Tesla data breach (2022): Hackers stole data from over 1 million Tesla vehicles, including vehicle identification numbers, VINs, and driving habits.
Samsung smart TV data breach (2021): Hackers were able to access and control millions of Samsung smart TVs, including webcams and microphones.
Nest thermostat data breach (2017): Hackers were able to access Nest thermostat data, including temperature settings and occupancy patterns.
Well, Facebook uses your data to learn who you are ie: your interests, your location, and much more. In this way, they are able to create a digital version of you. Almost all websites do this, done by storing small chunks of data (cookies) in your device that we can track. This is not the data we are talking about.
The future of data.
Data gives us the power to predict what will happen in the future or maybe things that are already happening yet we blindly miss them. Recently, Twitter shut down their free API pricing access to $5,000 per month to transact any meaningful business. A few weeks later, Reddit did the same. Why? The data. Whoever has this data has the moat to train the next human-like Artificial Intelligence.
 Today we have IOT Devices, Wearables, and smart devices all over. These devices collect a massive amount of data.
Today we have IOT Devices, Wearables, and smart devices all over. These devices collect a massive amount of data.
A smartwatch collects your steps, blood pressure, sleep time, and all personal data. Uploads this data to your account which is attached to your Email that holds more smart devices. The future will not rely on data from social media profiles but data from your devices that you gave freely. Data is more expensive than oil.
We can’t stop big tech firms from processing our data has to be protected. In this article, we’ll explore how this is done and should be done. I plead to you to accept the facts and keep in mind that most of your data is stored as raw data.
Homomorphic Encryption
Homomorphic encryption allows data to be stored as ciphertext. Data is not altered, allowing computations to be done on it. For instance, consider a healthcare scenario where medical data is encrypted, and computations can be performed on this encrypted data.
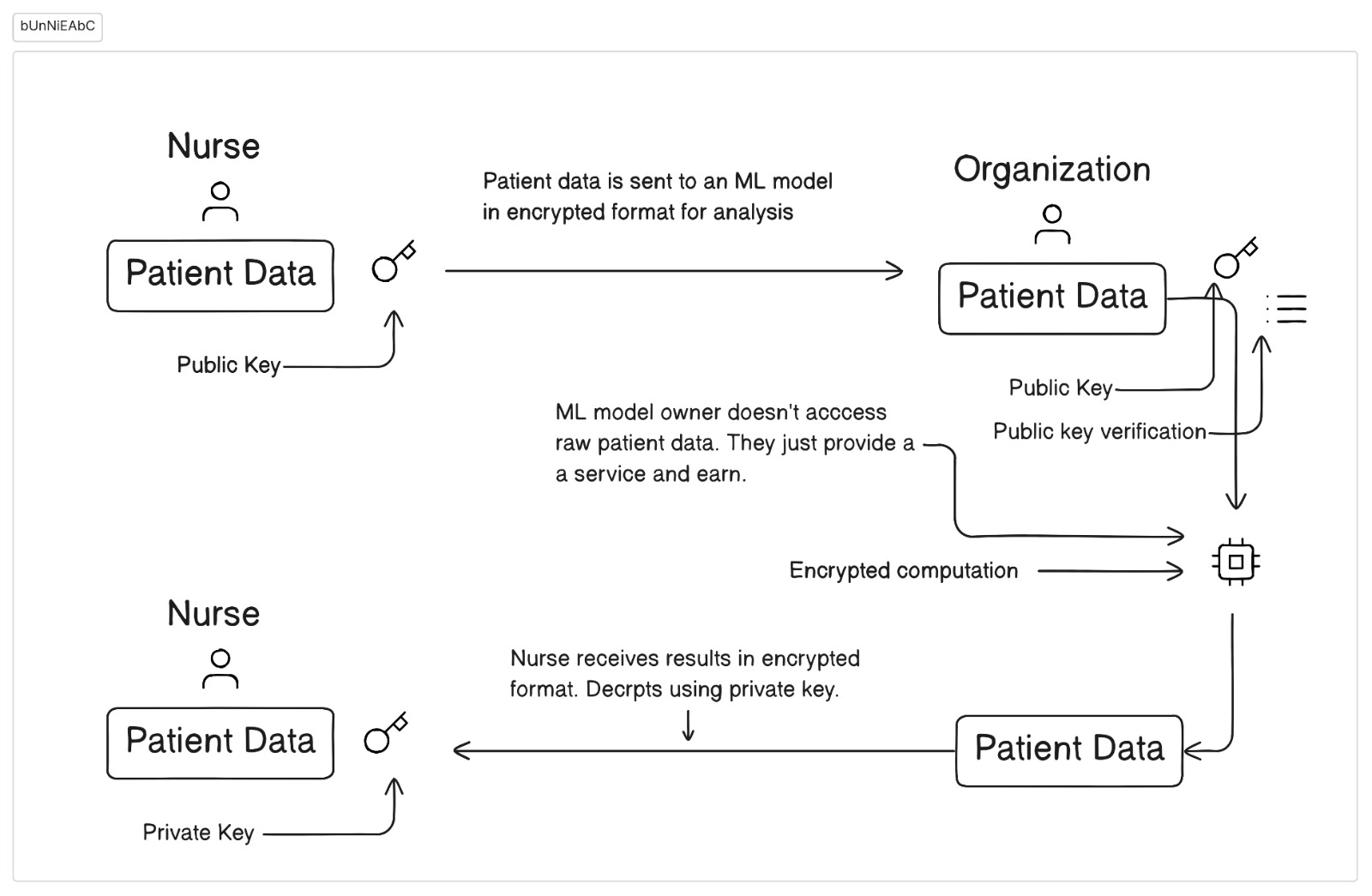 Notice how the ML service provider cannot access patients’ data, making it a secure way to utilize sensitive information while maintaining privacy.
Notice how the ML service provider cannot access patients’ data, making it a secure way to utilize sensitive information while maintaining privacy.
Zero-knowledge proofs (ZPFs)
ZPFs are protocols that allow a Prover to Verify a given statement without providing sensitive information but the statement itself. Worldcoin uses this same system to prove you are a unique human without Government identification. The World app uses your unique iris data to generate an iris hash, ensuring privacy while confirming uniqueness. I’d highly recommend you read this article: WorldCoin: The Cryptocurrency with a Unique Airdrop System
Data Minimization
Data minimization strategies aim to collect and retain only the data necessary for a specific purpose. This approach reduces the exposure of sensitive information and limits the risk of data breaches.
Blockchain Technology
Blockchain, known for its decentralized and tamper-resistant nature, is used for secure and transparent record-keeping. It can be applied in scenarios where data integrity and privacy are essential, such as supply chain tracking or healthcare records.
Federated Learning
Federated learning decentralizes machine learning processes. Instead of sending data to a central server, machine learning models are sent to the data sources (e.g., user devices). Models are updated locally, and only the model updates (not raw data) are transmitted. This approach preserves privacy by minimizing data exposure.
Government Oversight
Governments today oversee how citizen data is handled, which can sometimes distract from efficient service delivery. Striking the right balance between data protection and effective governance remains a challenge. Meanwhile, Zuck is chewing data and making cash to build the metaverse to make the world a better place.
